Passwords, part 3: Being a good liar
We covered how to create good passwords in part 1. Part 2 discussed the importance of having multiple passwords and how to manage them. Hopefully, you’ve taken these suggestions to heart and are already using them out in the real world. However, we’re not quite done. We still need to keep the bad guys from sneaking in the back door.
In 2008 a hacker broke into the Yahoo! email account belonging to Sarah Palin, a U.S. vice presidential candidate. It was remarkably easy to do. The hacker, a fellow named David Kernell, slid in through Yahoo’s password recovery facility, answering a security question with information about Palin’s personal life that was readily available online. Several years down the road, the rise of social networks like Facebook, Google+ and LinkedIn make it even easier to gather the data needed to get past a series of so-called “secret questions” because so many people leave the answers laying around out in the open.
There’s an easy solution to this dilemma: tell lies. If honesty is the best policy, this is the exception that proves the rule. These days, it’s best to assume your personal information is not safe. It may be deliberately or inadvertently exposed by yourself or by others, or it may simply be guessable. So, when a website asks you to answer a set of security questions (or challenge questions or secret questions or whatever they decide to call them), make stuff up. Come up with something memorable to you but not in the public record.
Here are some ideas…
- If you are a history buff, you might pretend to be Abraham Lincoln (adjust the birth date, though). Place of birth? Hodgenville
- I know of one guy who uses fruit names for everything. Name of your first grade teacher? watermelon
- One of the easiest tricks is to deliberately misspell your answers in a particular way — for example, always doubling the third letter. From what high school did you graduate? Wesstview
- Another fairly simple technique is to trade answers with your spouse, partner or significant other.
Bottom line: If you answer security questions honestly, they become insecurity questions. So, be imaginative with your answers. You don’t have to create a complete fantasy world, but you do need to bend reality at least a little bit.
Next up: Part 4 of this series (in progress) will cover a handful of more advanced topics for those of you who wish to dig more deeply into this whole password thing.
If you’ve read part 1 of this series, you should have a fair idea of how to create good, secure passwords. Problem is, to do a proper job you should employ multiple passwords. In theory, this means a completely different password for every place online that requires a logon of some sort. Every storefront, bank, social networking site, discussion forum and flea market should have its own unique password.
Yeah, right. Like that’s going to happen.
So, I am going to risk the wrath of all right-thinking security geeks and suggest some guidelines that, while not perfect, will tighten your security substantially without posing an undue burden on your day-to-day online activities.
Before I dive into the details, let’s take a brief look at why you need multiple passwords. It’s not at all unusual for someone to have logons at 30 or 40 different sites, very likely more. The more sites you’re on, the greater the chance that one of them will be hacked and the user names and passwords stolen. If this happens and you’ve used more or less the same logon everywhere, you have essentially handed the bad guys the keys to your entire online life. But, if each site has a unique password, your exposure is limited to just that one hacked site. Employing multiple passwords limits the damage.
Like most security issues, there is a trade-off between perfection and convenience. Managing a big pile of passwords is a nuisance, especially across multiple devices, but using the same password everywhere is a disaster waiting to happen. Happily for those of you who just want to get stuff done, there is a compromise technique that reduces risk considerably without undue management overhead.
The solution?
Use a different password for each major online category.
Depending on circumstances, you should have a minimum of five or six passwords:
- Maintain a unique, high-security password for banking functions. Use the rules from part 1, but ensure the password is at least 12 characters long. If you have credit cards that are not associated with your bank accounts, create a separate password for online access to those cards.
- Use a different, high-security password for social networks (Facebook, Google+, etc.). There’s always some dirtbag trying to break into such places because it lets them engage in all sorts of profitable mischief. Having some bottom feeder rummage through your — and your friend’s — personal details is a Bad Thing. The potential identity theft angle is even worse, especially if your social networking password also happens to be the same one you use everywhere else.
- Have a unique email logon. Again, follow the rules laid out in part 1.
- Use a separate password for shopping.
- And, finally, have at least one other password you use for everything else.
If this many passwords is too much of a burden, at least keep banking and social networking separate. It’s very important to keep those two fenced off from the rest of your online life.
There’s yet another piece to this puzzle. In part 3, we talk about the importance of lying. Turns out, there are times when telling the truth is detrimental to password security. After that, Part 4 (in progress) will examine a handful of more advanced topics, including some utilities you can use if “good enough” is not good enough and you really, really want to maintain a unique password for every site you visit online.
There are a couple of simple, basic rules for using passwords. Unfortunately, almost no one follows them. Still, we all need goals and aspirations, so here they are:
- Create passwords that are very hard to guess.
- Do not use the same password everywhere.
In other words, there are two things to worry about: creating good passwords and managing them. The first is pretty easy; organizing the second is a bit tougher.
In part 1 of this series, we’ll get the easy stuff out of the way: creating passwords the bad guys can’t crack. Part 2 talks about managing those passwords. Part 3 discusses the importance of lying (nice teaser, eh?). Lastly, if your eyes haven’t glazed over by then, you can also read part 4 (under development), which touches lightly on some of the technical background and on a few specialized topics.
A good password should have:
- at least eight characters, including
- at least one upper-case letter,
- at least one lower-case letter,
- at least one number
- and (if allowed) at least one character that is not a letter or number (“&”, “$”, “%”, “!”, etc.).
The idea here is to come up with a password that is too tough to crack. Following the “good password” rules is a good start, but a password also needs to be hard to guess. That being said, here’s some stuff to avoid, even if you follow the good password rules…
Do not obviously base a password on a real word or a proper name. In other words, if it is in the dictionary, don’t use it. The most common example is basing a password on the name of a child, grandchild or pet — just the sort of information an attacker could pick up from a Facebook page. (In my experience, almost half of all users do this.) The second most common is using the name of a favorite sport, sports team or a related phrase. Use some imagination. Mix it up a bit. Keep in mind that the bad guys are very shrewd guessers.
Do not use “leetspeak” (substituting a “3” for an “E”, “4” for “A”, “7” for “T”, etc.). The bad guys know this trick. “L37m31n” is just as obvious and easily cracked as “Letmein”.
Let’s wrap up with a few examples…
Edward123 — Technically, this meets the minimum “good password” requirements — it has both upper- and lower-case characters, as well as some digits — but it totally blows the “hard to guess” part. A proper name followed by a simple string of numbers is way too easy to crack.
ed48#wRD! — Not bad; should do the trick. It follows all the rules and, unlike the previous example, is not obviously inspired by your dog, Edward.
fc9asI9PP!e3 — Good one. It’s 12 characters long (the maximum allowed at some web sites), totally random, follows all the rules and is darn near impossible to crack. It’s also hard to type, but that might be a worthwhile trade-off on something like a banking site.
Alas, knowing how to build a good password is just a start. You need multiple passwords to do this security thing properly. We’ll talk about ways to handle that little problem in part 2.
(A brief note about passphrases: This is usually the point where someone gets the vapors because I haven’t mentioned passphrases. A passphrase is a long string of characters, usually in plain language. For example: “Mr. Thribbet paced the burning deck anxiously.” It’s easier to remember and type than an obscure, gobbledegook password and, because of its length, it is virtually impossible to crack. Trouble is, most sites won’t let you use a passphrase long enough to do you any good. We’ll discuss passphrases at more length in part 4 — coming soon eventually.)
The return of the undead cookies!
(Note: This post mentions web browser cookies. If you don’t know what those are, see the introductory paragraphs of the “Toss your cookies” article.)
Think you are protecting your privacy by pruning or deleting your web browser cookies? Chances are, you are sadly mistaken. According to a recent article on the Wired.com website, “more than half of the internet’s top websites use a little known capability of Adobe’s Flash plug-in to track users and store information about them.”
Flash is installed on something like 98% of the world’s personal computers. If you’ve ever viewed a web page, chances are you’ve encountered Flash in some form. Most videos are displayed with Flash, for example, as are the bulk of those animated ads you’ve trained yourself to ignore.
Problem is, Flash applications can store information on your computer in a widget called a Local Shared Object (LSO). Most of the time, the sort of stuff stored in an LSO is fairly benign, but this capability is also subject to abuse. The most egregious example of LSO abuse is something called “persistent cookies.” This was devised as a workaround to deal with the increasing number of people who, concerned with issues of online privacy, deleted their cookies regularly. A copy of the cookie data is stored in a Flash LSO. If the cookie has been deleted, it is restored using the LSO data.
This persistent cookie trick has been around for several years. When it was first proposed, the objections were so loud and fervent — even Adobe/Macromedia got huffy about it — it seemed the idea died an early death. I wrote it up for a small circle of friends, made some adjustments to prevent it and forgot about it. Evidently, bad things have been happening in the shadows since then and it is time to clean up my notes and post them online.
So, herewith are two straightforward ways to control Flash cookies with a minimum of hassle, as well as some information on when you should not remove Flash cookies…
Method #1:
Bring up the Flash Player Settings Manager web page.
On the second tab from the left, move the slider all the way to the left and place a checkmark next to “Never Ask Again.”
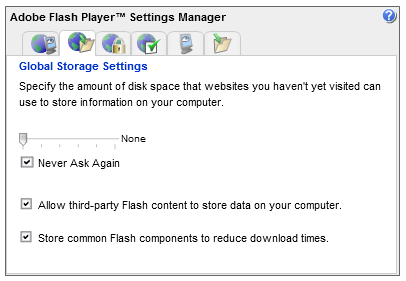
Next, go to the right-most tab and click the “Delete all sites” button.
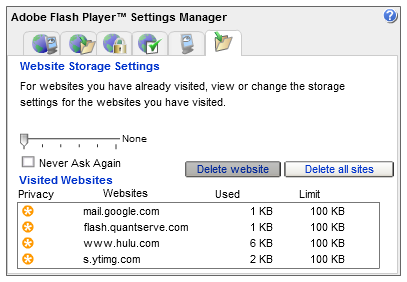
This procedure starts you with a clean slate and tells Flash that, in the future, sites can create Local Shared Objects, but only with zero length. In other words, a site can create an LSO, but it can’t store anything in it. Pretty sneaky, eh? I’d suggest you periodically revisit the right-hand tab and clear out the accumulated zero-size LSOs.
Advantage: Simplicity. No LSO storage means no Flash cookies.
Disadvantage: Some web sites use Flash LSO storage in a useful way. For example, certain video and audio sites employ LSOs to retain player settings during your visit or to help smooth out streaming video. Also, a very few sites will simply not work if LSOs are disabled. If this is a concern and you are using Firefox as your web browser, consider using Method #2 instead.
Method #2:
The above Settings Manager tweak stomps Flash cookies with minimal hassle and works with any web browser. However, if you are a Firefox user, there’s an add-on giving you finer-grained control. It’s called Better Privacy and can be found at http://netticat.ath.cx/BetterPrivacy/BetterPrivacy.htm. The easiest way to use Better Privacy is to set it to delete all LSOs when you exit Firefox.
Once you’ve installed Better Privacy, go to the Firefox Tools menu and chose “BetterPrivacy”. You’ll get a window that looks something like this:
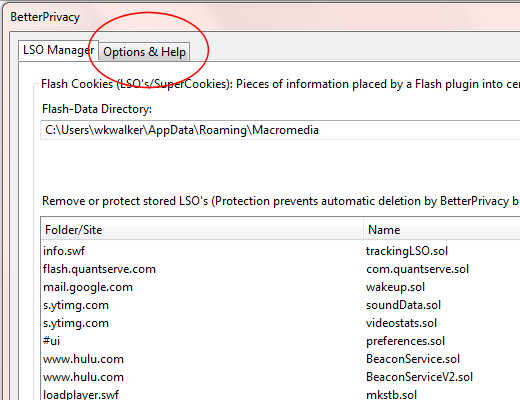
Click on the “Options & Help” tab. Enable “Delete Flash cookies on Firefox exit”. Optionally, disable (uncheck) “Always ask”. Personally, I always disable the “Always ask” option. Being asked what I wish to do with my Flash cookies every time I exit Firefox is a big nuisance.
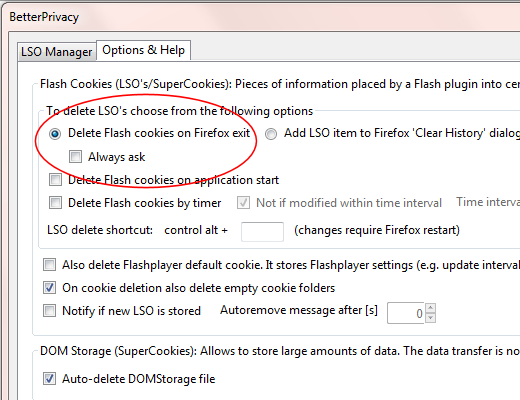
If you encounter the rare site that actually requires LSO storage to work properly (I’ve only seen one so far), using the Better Privacy add-on permits the site to allocate some space without the LSO persisting beyond your current browser session. You get the best of both worlds. Web sites are happy because Flash behaves in the expected way; you’re happy because all the Flash trash gets tossed when you exit Firefox.
But wait, there’s more.
Keeping good Flash cookies
Sometimes, you may wish to protect a Flash cookie from deletion. For instance, Flash-based games like the popular Machinarium store game progress and status in an LSO. Unless you thrive on frustration, zapping it would be a Bad Thing. Happily, a small additional tweak to the above Method #2 can accommodate this.
Launch Firefox and chose “BetterPrivacy” from the Tools menu. You’ll get a list of the current Flash LSOs that looks something like this:
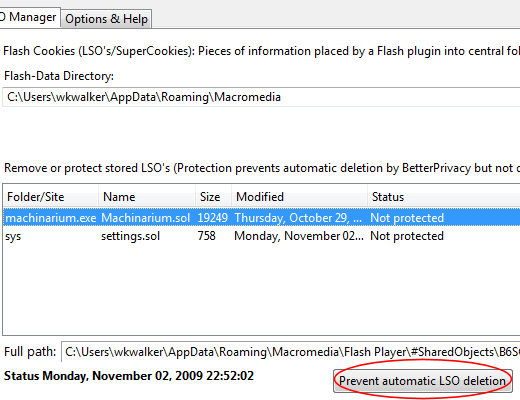
Select (click on) the LSO you want to preserve and click the “Prevent automatic LSO deletion” button. The LSO’s status will change from “Not protected” to “Protected Folder.”
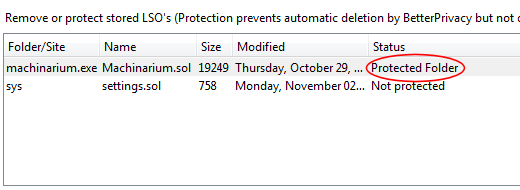
Click the “OK” button and you’re done. When you exit Firefox, all Flash cookies will now be deleted, except the ones you’ve protected. Unwanted Flash data still gets sent to that big bit-bucket in the sky, but your hard-won game progress remains undisturbed.
Best Firefox trick: Toss your cookies
If Firefox had no other special feature, I’d use it as my preferred web browser just for its cookie handling options.
For those of you who came in late, a “cookie” is a scrap of data that may be placed on your computer when you visit a web site. Web sites can only read and write their own cookies.
Used responsibly, cookies are very useful. For instance, most retail sites use cookies to keep track of the contents and status of your shopping cart.
Unfortunately, cookies are also subject to abuse. The most infamous examples are the so-called “tracking cookies.” Many web pages display advertising served up from third-party web sites. These third-party ad networks also deposit cookies on your computer. If you later visit another web site using ads from one of these outfits, they will read and update their cookies, in the process collecting information on what sites you’ve been visiting, what you looked at while you were there, the IP address you are using to access the Internet, the particulars of your web browser and a fair bit of information about your computing environment. The marketing droids say this is harmless and even beneficial because it enables them to provide advertising you are more likely to find useful based on your interests. Personally, I find it creepy that some anonymous outfit is building a profile of my browsing habits.
Some people deal with this by controlling what web sites are allowed to set cookies on their machines and under what circumstances. This gets tedious and often finicky. I prefer an easier approach.
Since its first release, Firefox has had an option to delete all cookies when you close the browser. Web sites can set any cookies they wish; everything works normally. When you exit Firefox, all the cookies disappear. Simple. Here’s how you do it in Firefox 3.5. Earlier and later versions are similar…
- From the Firefox Tools menu, Choose “Options…”
- Select the Privacy tab.
- In the History section of the Privacy window, tell Firefox to “Use custom settings for history”, put checkmarks next to “Accept cookies from sites” and “Accept third-party cookies”, and select the option to keep cookies until “I close Firefox”. You should end up with a Privacy pane that looks something like this:
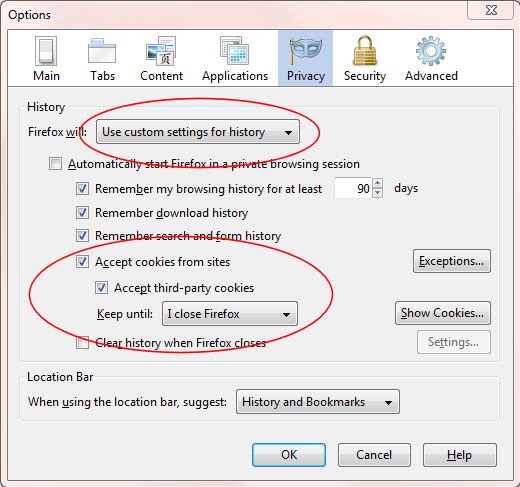
- Click the “Show Cookies…” button and go delete all your existing cookies. You may be surprised at how many are stored on your computer.
- Click the “OK” button to save your changes.
So, what’s the downside? Well, there are still a few web sites out there that store personalization information in cookies. Deleting your cookies every time you close out of Firefox will break these sites. However, this style of “portal” site went out of fashion quite some time ago. These days, most user-customized web sites store the personal settings on their servers and retrieve them when the user logs into the site.
For most people, the “toss your cookies” Firefox setting increases privacy with no significant effect on their web browsing experience.
There must be something about years ending in “7.” The last time Microsoft made significant changes to the file formats used by its Office suite was for the Office 97 release. They did it again for Office 2007. As Office 2007 becomes more popular, this is creating problems for people who are still using — and are perfectly happy with — older versions. It’s an issue for third-party packages, too, such as OpenOffice and WordPerfect Office.
Happily, there are solutions…
If you are using Office 2000, Office XP or Office 2003, download and install the “Microsoft Office Compatibility Pack for Word, Excel, and PowerPoint 2007 File Formats.” It’s free for anyone to download and requires no validation nonsense. According to Microsoft, “by installing the Compatibility Pack in addition to Microsoft Office 2000, Office XP, or Office 2003, you will be able to open, edit, and save files using the file formats new to Word, Excel, and PowerPoint 2007.” Do pay attention to the write-up on the download page, though, including the part about grabbing the latest security updates.
If you are using OpenOffice, just upgrade to the latest release (version 3.1 at the time this was written). It costs nothing and the update process is not unduly burdensome. If you’re running a fairly recent version of OpenOffice, you’ll likely be offered updates automatically.
If you are using WordPerfect Office X4 or later, you should be more or less OK. For earlier versions, contact Corel for compatibility information.
And, finally, if you’re using a non-Microsoft office suite and are not running Windows Vista or later, you’ll need the new Office 2007 fonts. See the “How to get the Office 2007 fonts” post for details.
How to get the Office 2007 fonts
(Note: If you need to open native-format Office 2007 documents, check out “Open Office 2007 documents without Office 2007.”)
Beginning with Office 2007 and Windows Vista, Microsoft introduced six new TrueType fonts. They are: Calibri, Cambria, Candara, Consolas, Constantia and Corbel. If you don’t have these fonts and open a document that uses them, it may not display properly. If the document is an Adobe PDF, you may, under some circumstances, see an unintelligible series of dots, accompanied by a message that one or more fonts is missing.
Fortunately, you don’t have to upgrade to the latest version of Microsoft Office, or move to Vista or Windows 7, to get the new fonts.
If you are running Windows XP or Windows 2000, but not any Office 2007 components, the easiest solution is to download and install PowerPoint Viewer 2007. The download is free and requires no validation checks. Installing the PowerPoint Viewer installs the new fonts as well. Simple.
And by the way . . .
Technically, this is a license violation but, if you want just the fonts without the PowerPoint Viewer, there is a way to do this. Here’s the general procedure:
- The PowerPointViewer.exe executable is actually an archive. Extract the contents to a new folder someplace convenient. 7-Zip and PeaZip can do this, as can the venerable, but non-free, WinZip.
- Take a look at the files you’ve just extracted and you’ll see yet another archive named ppviewer.cab, which contains the font files. Extract its contents.
- Use the Windows Control Panel “Fonts” applet to install the new fonts from wherever you placed the contents of ppviewer.cab. (Choose the “Install New Font…” option from the the “Fonts” applet’s File menu.) Make sure the “Copy fonts to Fonts folder” option is checked.
Running Linux? See this article.
I just bought a 500 gigabyte hard drive. When I go to “My Computer” and get the properties of the disk, it reports 465 gigabytes. Where’s the other 35 gigabytes?
A “disk manufacturer’s gigabyte” is not the same as a “computer geek’s gigabyte.” Generally, prefixes like kilo, mega and giga represent successive multiples of 1000. For example, “kilometer” means “1000 meters.” Similarly, mega indicates a million (1000 x 1000 = 1,000,000) and giga, a billion (1000 x 1000 x 1000 = 1,000,000,000). Computers, however, use binary arithmetic (base 2), so it is more convenient to use numbers that are powers of two. Thus, large computer-related quantities are usually expressed as multiples of 1024 (210). This means that a kilobyte (KB) is understood to be 1024 bytes rather than 1000 bytes, a megabyte (MB) is 1,048,576 (1024 x 1024) bytes, and so forth.
Hard drive manufacturers had a choice in the early days: They could use either the conventional meanings for these prefixes or the specialized, computing variant. Not surprisingly, they chose the alternative that gave them the bigger numbers. This is why that 500GB hard drive is viewed as a 465GB drive by your computer. A good rule of thumb is to take the advertised drive capacity and subtract a little over 5 percent. For terabyte drives, subtract about 10 percent.
Mind you, the folks who make those drives aren’t really cheating. My 500GB hard drive holds 500,096,991,232 bytes, which is, in fact, a solid 500 gigabytes in the outside world. What can I say? Computer people don’t think like normal people.
For the idly curious and numerically obsessed, here’s a table of the prefixes and their associated multipliers:
| Prefix | Conventional | Computing |
| kilo | 1000 | 1024 |
| mega | 1,000,000 | 1,048,576 |
| giga | 1,000,000,000 | 1,073,741,824 |
| tera | 1,000,000,000,000 | 1,099,511,627,776 |
| . |
By the way, non-geek terminology is used to describe most forms of mass storage, not just hard drives. For instance, the so-called “1.44MB” floppy is really a 1.38MB diskette and the “2GB” flash drive I carry around in my pocket actually stores 1.87GB.
